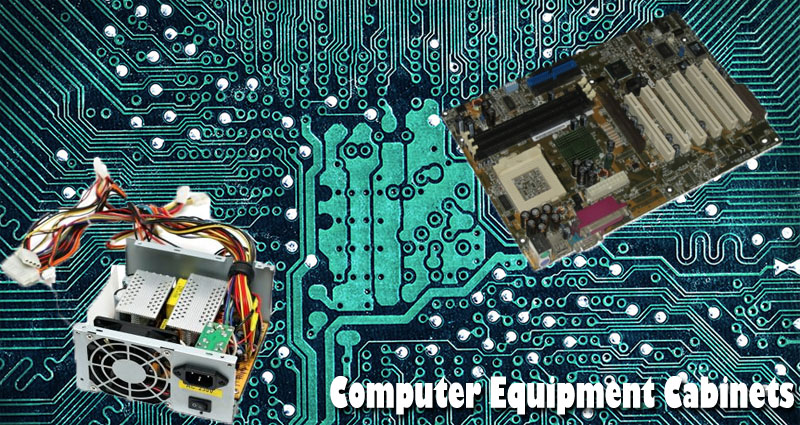
Computer systems have come to be an integral part of our life and whether it be inside the home, our offices, production homes, or possibly a computer software organization, the computer is a principal requirement for everybody. With the rising numbers in computer usage worldwide, the necessity for computer equipment cabinets is also increasing rapidly and becoming a need to have even for an individual user. The explanation behind finding a cabinet for your computer hardware is always to make sure appropriate storage in the solutions and, also, making them last longer.
Computers are certainly not just a box and also a monitor any longer, they’ve many computer accessories apart from a CPU & Monitor. Additional hardware components like a printer, scanner, joystick, external drives, additional servers, etc. have all become important parts of the computer nowadays, and hence require additional cabinet Room for safe storage & uncomplicated maintenance.
A computer gear cabinet also addresses the issue of Room shortage, which is usually a prime concern for most of your companies that use computers daily, examples of this involve application makers, BPO companies, trading companies, banks, and offices, etc. For the reason of its compact size, it stores all the equipment in vertical arrangements meaning less Room used and allowing the user convenient running of their business.
With swiftly growing demands, there are lots of manufacturers offering cabinets with excellent designs & utilities. The cabinets being produced are manufactured with advanced techniques employing digital design methods to produce a premium quality product. You will discover a lot of alternatives readily available around the market according to your specific needs, these also come with very affordable price tags at the same time.
To conclude, a high-quality computer gear cabinet is a must to place on your computer hardware purchase list. In the event you are obtaining additional accessories to go with the computer, then you’ll wish to make sure to invest in your computer and added accessories.
Are Your IT Systems Safe?
An E-mail has changed the planet of communication for corporations, but it is also confirmed to become highly vulnerable to outside influences. Hackers, scammers, and identity thieves are often on the market placing your business in danger. All it takes is for one particular employee to open an e-mail attachment for a virus to infect your entire network or worse, give unauthorized access to your business’ confidential information and facts. So how are you able to maintain your business safe?
Strategies for finding the ideal computer network security
Employ a computer safety consultant
When it comes to IT security services, skilled protection cannot be overrated. With enterprise information concerns, you can’t afford to wait for your computer network safety to become compromised ahead of taking action. A computer safety consultant can customize experienced computer security options to help you reduce enterprise information dangers, avoid data breaches and personal facts leaks, and address safety dangers and malware before you wind up becoming a victim.
Create secure IT systems
A computer safety consultant can assist protect you from hackers by designing computer network safety that is constructed about restricted access to your technology infrastructure. Do not let the notion of convenience provide you with a false sense of safety in terms of who must have access. The number of individuals with access to all your systems, equipment, and software needs to be limited to you as well as your most trusted staff. And the finest computer safety solutions reduce dangers using an exceptional set of e-mail addresses, logins, and servers for each user or department.
Guard your self with passwords
A password may be the 1st line of defense against unauthorized access to your computer systems and networks. But use a weak password, and you make it that much less complicated for an attacker to acquire access. All sensitive information, gear, and wireless networks should be protected with exceptional usernames and passwords for particular folks. Powerful passwords are harder to crack, even together with the newest password-cracking software. Your password should include letters, numbers, and symbols, and it should not be straightforward to guess. And should you come about to create a document listing all corporation passwords, it’s essential to encrypt that with its password as well.
Inoculate your systems with anti-virus computer software
Each computer is vulnerable to various viruses, worms, and trojans that lurk on the web. These malicious software programs can wreak havoc on your computer network security, damaging your computer and files, and even stealing passwords and stored data. Obtain a superb anti-virus software program and make sure that it’s usually as much as date. Some network providers even supply this free of charge. Also, check to see that your anti-virus software checks for spyware, adware, and any other malware that could be hiding on your computer.
Hold confidential information by yourself network
Though Cloud computing assists firms to strengthen efficiency and cut charges, there are risks involved. The third parties who home your information on remote servers usually have their very own security troubles. When it comes to IT security services, have your computer security consultant preserve your confidential data by your network. Maintain it off the Cloud.
Thoroughly screen, monitor & train staff
You can not predict when or if an employee will betray your trust, but you can put safeguards in place for computer network security to help decrease the damage ought to this be the case. 1st, thoroughly screen your staff before hiring them, especially if they’ll have access to financial or confidential business information and facts. Limit the number of employees that can access this data, and password-protect those files. Change the passwords generally to help prevent former employees from accessing your business networks. It is amazing how many networks are hacked or crashed simply because staff never follow documented procedures. Solid training must be provided upfront and as needed to help this become second nature.
Ignore unknown e-mail attachments
The easiest way to get a virus, trojans, or worms is to download an infected file. Never click on unsolicited e-mail attachments. When you want to download the file, confirm the attachment’s contents together with the sender. In case you never know the sender, it is most effective to just delete the message. This goes a long way when it comes to computer safety solutions.
Trying to scrimp in regards to your small business computer network safety can be a costly mistake. It is significant to know what your business is up against and take steps toward prevention. Hire a computer security consultant with customized computer safety solutions to assist you through the process. The investment will give your company the IT security services necessary to preserve your facts secure and your business successful.